

我正在通过我的MVC/Durandal web应用程序将身份证件保存到Azure blob存储中。我正在按照这个例子对Azure存储中的blob进行加密,使用Azure密钥存储库来存储加密秘密。
下面是我的代码:
public async Task UploadIdentityDocumentForClient(string fileName, ParsedClientModel parsedClientModel)
{
BlobRequestOptions options = await GetBlobRequestOptions();
await
_storageRepository.CreateEncryptedBlobFromByteArray(_storageManager, _containerName, fileName, parsedClientModel.IdentityDocumentFile, parsedClientModel.IdentityDocumentContentType, options);
return fileName;
}
private static async Task GetBlobRequestOptions()
{
string secretUri = WebConfigurationManager.AppSettings["SecretUri"];
string secretName = WebConfigurationManager.AppSettings["SecretEncryptionName"];
*1 KeyVaultKeyResolver keyVaultKeyResolver = new KeyVaultKeyResolver(GetAccessToken);
*2 IKey rsaKey = keyVaultKeyResolver.ResolveKeyAsync($"{secretUri}/secrets/{secretName}", CancellationToken.None).GetAwaiter().GetResult();
BlobEncryptionPolicy policy = new BlobEncryptionPolicy(rsaKey, null);
BlobRequestOptions options = new BlobRequestOptions
{
EncryptionPolicy = policy
};
return options;
}
public static async Task GetAccessToken(string authority, string resource, string scope)
{
string clientId = WebConfigurationManager.AppSettings["ClientId"];
string clientSecret = WebConfigurationManager.AppSettings["ClientSecret"];
ClientCredential clientCredential = new ClientCredential(clientId, clientSecret);
AuthenticationContext authenticationContext = new AuthenticationContext(authority, TokenCache.DefaultShared);
AuthenticationResult result = await authenticationContext.AcquireTokenAsync(resource, clientCredential);
if (result == null)
{
throw new InvalidOperationException(
"GetAccessToken - Failed to obtain the Active Directory token for application.");
}
*3 return result.AccessToken;
}
public async Task CreateEncryptedBlobFromByteArray(IStorageManager storageManager, string containerName, string fileName,
byte[] byteArray, string contentType, BlobRequestOptions options)
{
CloudBlobContainer container = await CreateStorageContainerIfNotExists(storageManager, containerName);
CloudBlockBlob blob = container.GetBlockBlobReference(fileName);
blob.Properties.ContentType = contentType;
await blob.UploadFromByteArrayAsync(byteArray, 0, byteArray.Length, AccessCondition.GenerateEmptyCondition(), options, new OperationContext());
}
这条线。。。
IKey rsaKey = keyVaultKeyResolver.ResolveKeyAsync($"{secretUri}/secrets/{secretName}", CancellationToken.None).GetAwaiter().GetResult();
总是返回NULL。
我在上面的代码中添加了断点(*1到*3),并且注意到*2总是在*3之前被命中。这意味着KeyVaultKeyResolver(GetAccessToken)调用不等待GetAccessToken调用返回值。
知道我做错了什么吗?
我发现我做错了什么。
如果断点2是,我应该使用以下代码:
SymmetricKey sec = (SymmetricKey) cloudResolver
.ResolveKeyAsync("https://yourkeyvault.vault.azure.net/secrets/MiplanAdminLocalEncryption",
CancellationToken.None)
.GetAwaiter()
.GetResult();
我还必须使用PowerShell将这个秘密添加到我的Azure密钥库中。通过管理UI创建机密不起作用。下面是我使用的命令:
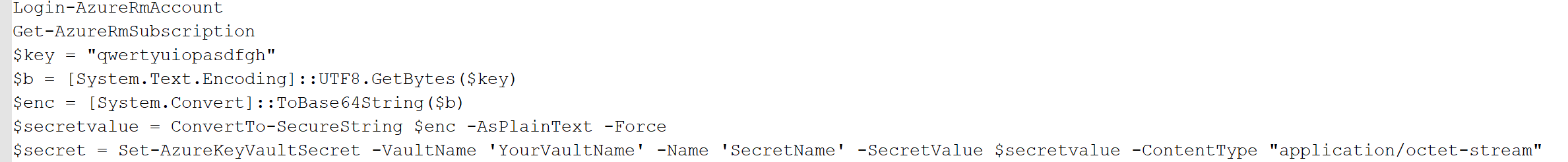
对不起,图像,但因此将不接受以上文本,即使当粘贴为代码示例。
请参见此站点获取原始示例。
我找到了一个通过Azure传送门添加秘密的方法:
//If entering via Azure UI:
//Your secret string must be 16 characters (28 bits) long or end up being 28, 192, 256, 384, or 512 bits.
// Base64 encode using https://www.base64encode.org/
//Take this encoded value and enter it as the secret value in the UI.